Safeguarding Data: 10 Critical Steps for MSPs and Marketing Agencies
By: EmMa Matern
September 6, 2023INTRODUCTION
There are few trends in the direct mail marketing world, and the marketing-communications (marcom) world that are growing faster than the renewed focus on data security. As increased granularity of data allows for greater personalization, and the power of data to drive results in marketing grows exponentially, the importance of safeguarding that data is top of mind for any mail service provider.
With thousands of cyber attacks per day, constant phishing attempts, and ransomware attacks on organizations large and small having become a ubiquitous part of working in the digital age, it’s crucial that anyone who is working with data have a plan to keep that data secure.
At Postalgia we work with MSPs (those are Mail Service Providers), as well as marketing agencies, who need to worry about securing not just their own internal data, but also the data of their clients.
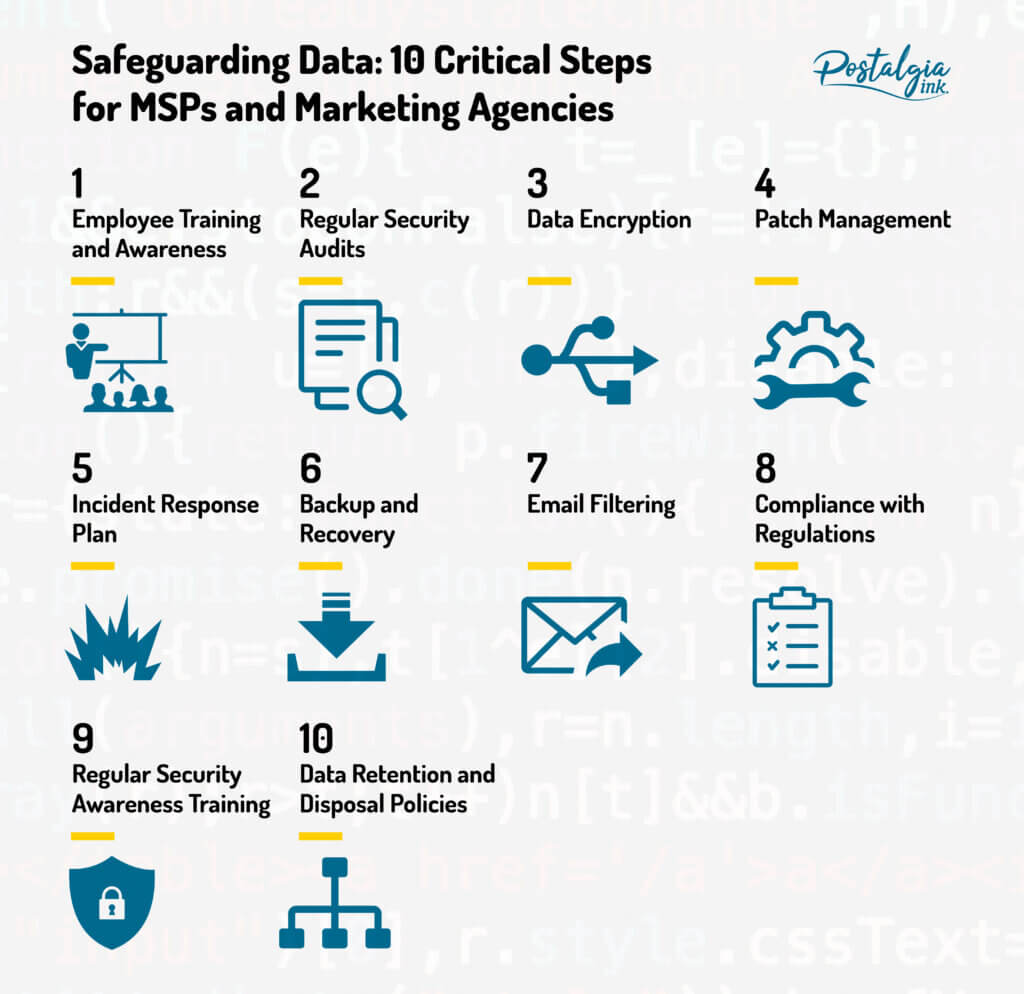
Key Topics
1. How to Maintain Employee Training and Awareness?
2. Why Perform Regular Security Audits and Assessments?
3. How Does Data Encryption Secure Data?
4. How to Ensure Software Patch Management?
5. Why you Need an Incident Response Plan?
6. Why a Data Backup and Recovery Solution is Critical?
7. Why Implement Email Filtering and Anti-Phishing Measures?
8. What are the Relevant Regulations for Mail Service Providers?
1. How to Maintain Employee Training and Awareness?
There is no defense against cyber attacks more important that a well-trained and vigilant staff. That’s because most cyber attacks rely on at least some level of human intervention – a staff member giving up a password, or sending an unsecure email.
It’s important that your staff know what they’re looking for – that means making them aware of the latest methods of hackers.
Similarly, any tool that you’re looking to employ is only as good as the staff operating it. Your training and education should be regular, it should be clear, and it should come with some kind of testing or auditing to ensure that staff have internalized the information that you’ve communicated to them.
It’s always a good idea to use a 3rd party cybersecurity consultant or expert to provide regular training to your entire team.
2. Why Perform Regular Security Audits and Assessments?
You don’t know what you don’t know, and so sometimes to stop a thief, you need to think like a thief. That means that in addition to regular training, you should be doing regular testing, audits, and cybersecurity assessments.
From penetration testing (having a cybersecurity expert attempt to break through your defenses on your behalf to illuminate your weaknesses) to vulnerability scans, as well as holistic physical and digital cybersecurity audits, your organization, your mail service providers, and any other company that touches your data, should be employing cybersecurity experts to regular test their defenses by trying to break through them.
3. How Does Data Encryption Secure Data?
Encryption essentially ensures that your data won’t be readable if it falls into the wrong hands. There are two types of encryption: encryption at rest, and encryption in transit.
Encryption at rest is how you encrypt your data when it is sitting on your computer, your servers, or otherwise proverbially “at rest” (ie: not moving).
Encryption in transit makes sure that your file will be likewise unreadable by the wrong eyes (anyone without the decryption code or password) when it’s being sent from one location to another.
Both are crucial for any organization that is serious about protecting their sensitive data.
4. How to Ensure Software Patch Management?
Software providers are regularly offering patches (fixes or updates that solve new or newly discovered bugs) that can be used to keep software up-to-date and prevent vulnerabilities from being exploited.
Any organization dealing with sensitive data must have a strategy for regularly updating all software that they depend on.
5. Why you Need an Incident Response Plan?
Even the most well-prepared organizations can fall victim to cyber attacks, so it’s crucial that any company, MSP, agency, or mail house that you work with has an incident response plan to prevent them having to scramble during a time when every minute counts.
The plan should identify key individuals and their responsibilities for responding to incidents (whether their job is identification of problems, shoring up of defenses, mitigating fallout, or communicating with stakeholders).
The plan should include ways to contain and mitigate data leaks, address the source of the attack or leak, communicate with key individuals affected by the leak, recover from the leak to get systems back online and operations up and running as before, and learn and communicate lessons from the incident.
6. Why a Data Backup and Recovery Solution is Critical?
It’s important that any organization that has data is backing them up – because as bad as a cyber attack can be, the intentional or accidental loss of data can be just as bad.
Key considerations include how often you’re backing up your data, where it’s being stored, whether it’s being backed up automatically or manually, and whether you’re able to easily recover lost data.
The last consideration needs to be tested regularly, to ensure that it works when you need it.
7. Why Implement Email Filtering and Anti-Phishing Measures?
Phishing is one of the most common methods for hackers and scammers to improperly access data that don’t belong to them.
One of the easiest ways to access data that are encrypted is to simply get someone to give you their password. That often means misrepresenting intentions or pretending to be someone that they’re not.
In addition to education and training, there are myriad anti-phishing tools available, many of them native to different email providers.
Similarly, robust policies can prevent phishing. For example, a policy that prevents employees from giving out passwords without the approval of two different managers, or a waiting period of 24 hours.
8. What are the Relevant Regulations for Mail Service Providers?
Staying in alignment with pertinent regulations like GDPR or HIPAA, is essential. Not only is a good idea to pick a mail service provider that is familiar with cybersecurity standards, but it’s also important to pick one that is familiar with the laws governing your industry. For example, if you’re an American hospital or healthcare provider with access to patient data, you’re likely subject to HIPAA.
Safeguarding data can be an arduous and expensive process. Picking a mail service provider that can help you manage the transfer and use of your data can save you a lot of time and money. Non-compliance can lead to severe consequences, including substantial fines and reputational damage.
9. Why is Regular Security Awareness Training Important?
As important as knowing how to backup data, it’s equally if not more important to know when and how to dispose of data.
Automatic data disposal is an important part of any cybersecurity plan.
Key considerations include: Which data should be disposed of, how long after use, and should this happen automatically or manually?
10. Why are Data Retention and Disposal Policies Needed?
To ensure robust data security, organizations must begin by establishing well-defined data retention and disposal policies. These policies serve as guidelines for how long different types of data should be retained and when they should be safely disposed of. By having clear policies in place, companies create a structured framework that governs the lifecycle of their data, from its creation to its eventual removal.
Regularly reviewing and securely disposing of data that is no longer necessary is a fundamental step in maintaining data security. As information accumulates over time, retaining data that is no longer needed increases the risk of a potential data breach. The principle of data minimization becomes pivotal here – organizations should retain only the data that serves a legitimate purpose and dispose of the rest. By doing so, the potential impact of a data breach is significantly reduced, as there’s less sensitive information at risk of exposure.
CONCLUSION
Data breaches and cyber threats have become commonplace, the responsibility of safeguarding sensitive information has never been more critical for MSPs and Marketing Agencies. By meticulously implementing the ten steps outlined in this post, these entities can create a formidable defense against potential vulnerabilities. From educating staff and clients to adopting advanced security technologies, the path to robust data security demands constant vigilance, proactive measures, and a commitment to staying ahead of the evolving threat landscape. As companies embrace these strategies, they not only protect their own reputation and business continuity but also foster trust among clients, positioning themselves as defenders of digital security. Ultimately, by prioritizing data security, these entities pave the way for sustainable success in an increasingly interconnected and risk-prone digital world.
At Postalgia, we prioritize data security above all else. We recognize the sensitive nature and importance of your data, and we go beyond standard measures to ensure its complete protection. Our security protocols involve robust strategies aimed at preventing unauthorized access and data breaches, ensuring the highest levels of confidentiality and integrity throughout every step of the process.
In a time where the consequences of data breaches can be far-reaching, our dedication to data security goes beyond mere policy; it stands as a commitment to safeguarding your interests. We comprehend that the faith you entrust in us forms the foundation of our relationship. It’s this very trust that drives us to cultivate an environment where your data is housed with the utmost security.
